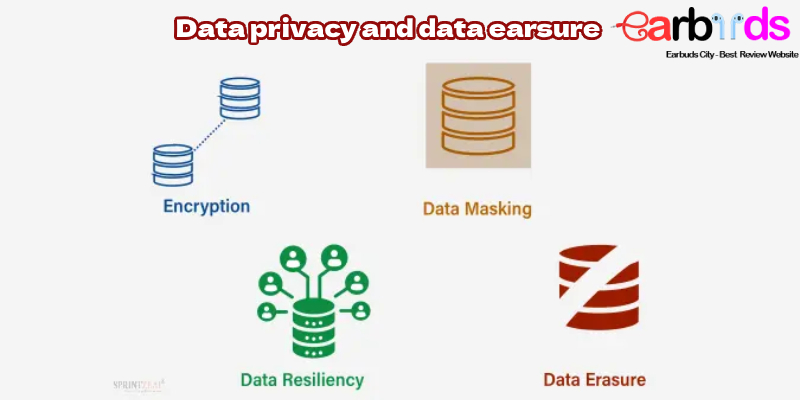
Data privacy and data earsure are increasingly innovating to meet the challenges of today’s digital environment. Let’s learn us about its advantages and disadvantages.
What is data security?
Data Security is the process of protecting information from unauthorized access, alteration, or destruction. The main goal of data security is to ensure that data is protected from risks such as unauthorized access, improper alteration, or loss.

Meaning of data privacy
Protecting Personal Privacy
Data privacy protects users’ personal information from improper collection, processing and use. This helps ensure that users have control over their personal information.
Preventing Information Abuse
Data privacy prevents the misuse of personal information for improper purposes, such as over-targeted marketing, fraud, or other harmful actions.
Building a Spirit of Trust
Respect and compliance for data privacy creates trust between businesses and users. Users feel secure knowing their personal information is treated properly and securely.
Control Instruments
Data privacy gives users the ability to control their personal information. They can determine what information is shared, with whom, and for what purpose.
Prevent Cyber Security Risks
Protecting data privacy helps prevent cybersecurity risks, such as hacker attacks, unauthorized access to systems, and loss of important information.
Compliance with Law
Data privacy is closely related to compliance with regulations and laws on personal information protection, such as GDPR (Europe), CCPA (California), and many other regulations around the world.
Encouraging Innovation and Technological Development
Protecting data privacy stimulates innovation and growth in the technology sector, as businesses must seek creative solutions that protect personal information while maintaining flexibility and convenience.
So do you know about data privacy and data earsure? Keep scrolling.
The role of data deletion in information security
Privacy Protection
Data deletion ensures that personal information no longer exists when it is not needed, keeping user privacy guaranteed.
Prevent risks from using personal information for improper or unauthorized purposes.
Compliance with Laws and Regulations
Many laws and security standards require the deletion of data when it is no longer needed for the previously identified purpose.
For example, GDPR (General Data Protection Regulation) requires businesses to delete personal data when it is no longer used for the stated purpose.
Prevent Cyber Security Risks
Data deletion is an effective way to prevent cybersecurity risks. When data is no longer needed, keeping it only creates potential target points for attack actions.
Effective Data Management
Deleting data helps manage information and resources more effectively. It helps relieve storage pressure and facilitates flexibility in data management.
Data Loss Prevention
Periodically deleting data helps prevent data loss due to technical problems or cyber attacks. This includes performing regular backups and deleting outdated data.
Creating the Foundation for Data Management Standards
Data deletion is an important part of data management standards. It helps build the foundation for robust data management processes and ensures data integrity.
Handling Termination of Business Relationships
In a business relationship, data deletion can mark the end of a relationship and help ensure that related information is no longer used after the relationship ends.
So do you know about data privacy and data earsure? Keep scrolling.
Data privacy and data earsure: Regulations and standards
GDPR (General Data Protection Regulation)
Regulations
Widely applied in the European Union, GDPR sets strict regulations on the collection, processing, and security of users’ personal information.
Standard
Requires businesses to implement strong security measures, clearly communicate data usage, and ensure user privacy.
CCPA (California Consumer Privacy Act)
Regulations
Applies to organizations that collect personal information of consumers in the state of California, USA. CCPA provides consumers with control over their personal information.
Standard
Require businesses to provide consumers with control over personal information, including the right to data deletion.
ISO/IEC 27001 – Information security management system
Regulations
International standard that specifies requirements for establishing, implementing, and maintaining an effective information security management system.
Standard
Requires risk assessment, access management, implementation of physical and logical security measures, and maintenance of continuity in information security management.
NIST SP 800-88 Rev. 1 – Guidelines for Media Sanitization
Regulations
Originating from the US National Agency for Standards and Technology (NIST), this document provides guidance on wiping information on storage media.
Standard
Identify effective data deletion methods to prevent information recovery and ensure the integrity of the deletion process.
HIPAA (Health Insurance Portability and Accountability Act)
Regulations
Applies to organizations and individuals dealing with health information in the United States. HIPAA protects the privacy and security of medical information.
Standard
Sets requirements for health information security, access control, and patient privacy protection.
PCI DSS (Payment Card Industry Data Security Standard)
Regulations
Developed by the Payment Card Industry Association, PCI DSS applies to organizations that process payment card information.
Standard
Require security measures such as payment card data encryption, access controls, and risk management.
So do you know about data privacy and data earsure? Keep scrolling.

Data privacy and data earsure: Advantages and Disadvantages
Advantage
Privacy Protection
The data deletion process ensures user privacy, preventing improper use of personal information.
Compliance with Law
Helps organizations comply with legal regulations such as GDPR, CCPA, and other data protection standards.
Prevent Cyber Security Risks
Data deletion helps reduce cybersecurity risks by eliminating potential target points for attack actions.
Effective Data Management
Helps manage information more effectively, reduce storage pressure and optimize system resources.
Increased Flexibility
Allows organizations flexibility in managing and processing data according to requirements and changing needs.
Defect
Loss of Important Information
The data deletion process can result in the loss of important information if not done properly.
Costs and Resources
Implementing a data deletion process can be costly and resource intensive, especially for large systems.
Resilience
In some cases, data can still be recovered, especially if the deletion process is not done carefully.
Facing the Difficulty of Complete Removal
Some types of data, such as data stored on cloud storage devices, may be difficult to completely erase.
Complex Requirements
The data deletion process sometimes requires complexity in identifying, classifying and processing data, especially when there are many different data sources.
Difficulty in Processing Big Data
Deleting large data can be difficult and requires careful planning to avoid impacting system performance.
So do you know about data privacy and data earsure? Keep scrolling.

Data privacy and data earsure: Technological evolution and future trends
Technological Progress
Encryption and Blockchain
Advances in data encryption and the use of blockchain technology to enhance data integrity and security.
Artificial Intelligence (AI) and Machine Learning (ML)
The integration of AI and ML in detecting risks, predicting user behavior, and enhancing attack recovery.
Edge Computing
Edge computing helps process data right at the source, minimizing data transmission over the network, while providing security and data management benefits.
Zero Trust Security
Zero Trust security systems do not trust any source and require continuous confirmation, protecting data from internal and external attacks.
Identity and Access Management
Advances in identity management (IAM) and access management, help organizations tightly control access and protect personal information.
Future Trends
Self-Securing Data
Data will be self-organizing and self-secure, using autonomous technology to recognize and respond to risks without human intervention.
Self-Sovereign Identity
Users will have the right to control and manage their personal information independently, reducing dependence on large organizations.
Quantum-Safe Cryptography
Develop cryptographic methods that are safe from the impact of quantum computers, ensuring data security in the future.
Collaborative Security Data
Organizations will proactively share security risk information to enhance detection and response capabilities.
Automatic Data Classification
Advances in automating content-based data classification help ensure data management meets regulations and standards.
Data Security in the Internet of Things (IoT)
Enhance security for IoT devices to prevent attacks from potential weaknesses in the system.
So do you know about data privacy and data earsure? Keep scrolling.
In conclusion
Data privacy and data security are not only an important part of information security, but also help businesses comply with the law, protect privacy, and manage information effectively.